European-Japanese Cybersecurity in the GNSS downstream user market


The European Union and Japan both continue their cooperation on developing and hardening commercial applications in regards to the GNSS downstream market segments. This does not only relate to technological improvements, but also the latest decisions, recommendations, and amendments related to Cybersecurity and Privacy obligations in Europe and Japan.
The user segment for Location Based Systems in the GNSS downstream market is rapidly growing as it plays a significant role in the technological development of future strategies such as Society 5.0, introduced by the former Japanese Prime Minister Shinzo Abe, or the growing demand for solutions accelerated though the current pandemic.
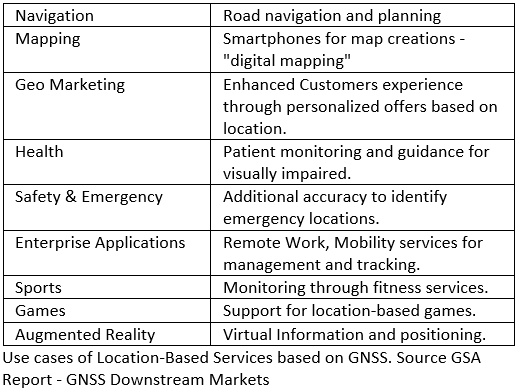 |
Location Based Systems offer a variety of use cases such as public health applications, for instance, the European Union Agency for the Space Programme, EUSPA (former GSA), is maintaining a list of Galileo based applications to monitor the COVID-19 outbreak.
Due to the growing demand for digitalisation and usage of GNSS related applications, it is crucial to look at the big picture when outlining such architectures, as services like this add additional complexity to an already complex environment. This means the necessity for security measurements and compliance towards data protection laws e.g. the EU – General Data Protection Regulation (GDPR) or Japan – Act on the Protection of Personal Information shall be considered. |
Especially where architectural parts are outsourced to external suppliers and providers it is a necessary task to verify used technology stacks in order to build robust applications, as well as to ensure contractual and organisational measurements to empower accountability at any time.
Trust in Data Matters
As applications rely on the accuracy provided by GNSS, maintaining trust in the information such as Position, Velocity and Time information (PVT) is crucial.
|
|
|
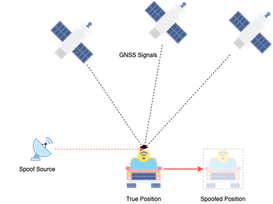
What is Spoofing?Spoofing tricks a GNSS receiver with false PVT information. The spoof source will broadcast signals with the same frequency and structure, therefore, disguising itself as a true GNSS Signal. Attack Scenario?Applications relying on PVT can be manipulated through misinformation e.g. targeting an AI system by feeding the algorithm with false information. |
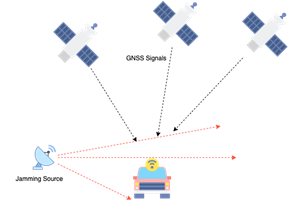
What is Jamming?Jamming interferes with the GNSS signal reception to block the GNSS signal from reaching the receiver. Such technology is available to anyone and depending on the power of the transmitter the range of effectiveness can vary from meters to kilometres. Attack Scenario?By disrupting the service through jamming, the application can stop working or can be limited in its performance. |
|
Outlook
To counter the risk of false information, Galileo will add additional robustness through the data authentication function Open Service Navigation Message Authentication (OS-NMA), which is currently in the public observation test stage and open for registration. This is a necessary step to counter spoofing attacks and to ensure trust in the data source, but it needs to be considered that it does not protect against signal jamming.
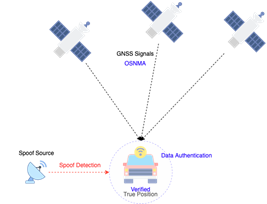 |
Furthermore, it is just one part of this fast-growing ecosystem. ICT infrastructure nowadays is better integrated, connected, and easier to access. Hyperscaler already offers first ground station to datacentre services, which enables them to directly connect to other services like machine learning, analytics, computation, storage etc. inside the CSP infrastructure.
Therefore, developers, as well as manufacturers in the space industry, need to invest in transparent and secure supply chains to identify potential vulnerabilities. |
The zero-trust approach can greatly increase the resilience of every single company in a supply chain and add stability to these growing networks. Instead of assuming that a company or product is safe, a zero-trust approach requires a review of all assets. By examining vendors and all other factors inside and outside the corporation as well as regular training for employees, it is possible to master those challenges.